In my previous post, I covered route filtering and mainly the use of ACLs, Prefix Lists, Distribute Lists, and Route Maps to filter routes. As an example on how to apply these, I also went through some route redistribution, between OSPF and EIGRP. In this post I’ll go more in depth on redistribution.
Although using a single routing protocol throughout an enterprise might be preferred,
many enterprises use multiple routing protocols because of business mergers and acquisitions, organizational history, or in some cases for technical reasons. Route redistribution allows one or more routers to take routes learned through one routing protocol and advertise those routes through another routing protocol so that all parts of the internetwork can be reached.
To perform redistribution, one or more routers run both routing protocols, with each
routing protocol placing routes into that router’s routing table. Then, each routing protocol can take all or some of the other routing protocol’s routes from the routing table
and advertise those routes. I’ll begin by looking at the mechanics of how to perform redistribution.
The redistribute router subcommand tells one routing protocol to take routes from
another routing protocol. This command can simply redistribute all routes or, by using
matching logic, redistribute only a subset of the routes. The redistribute command also
supports actions for setting some parameters about the redistributed routes, for example, the metric.
Setting Metrics, Metric Types, and Tags
Metrics must be set through configuration when redistributing into RIP and EIGRP,
whereas OSPF uses default values. The redistribute command under rip used hop counts.
The EIGRP metric in the redistribute command must include all five metric components, (Bandwidth, Delay, Reliability, Load and MTU), even if the last three are ignored by EIGRP’s metric calculation (as they are by default). The redistribute rip metric 1544 5 255 1
1500 command lists EIGRP metric components of bandwidth, Delay, Reliability, Load, and
MTU, in order.
OSPF defaults to cost 20 when redistributing from an IGP, and 1 when redistributing from BGP.
The redistribute command redistributes only routes in that router’s current IP routing
table. When redistributing from a given routing protocol, the redistribute command
takes routes listed in the IP routing table as being learned from that routing protocol.
Interestingly, the redistribute command can also pick up connected routes. For example,
R1 has an OSPF route to 15.1.2.0/24, and a connected route to 15.1.1.0/24. However, R3
(RIP) and R4 (EIGRP) redistribute both of these routes—the OSPF-learned route and one
connected route—as a result of their respective redistribute ospf commands. As it turns
out, the redistribute command causes the router to use the following logic to choose which routes to redistribute from a particular IGP protocol:
1- Take all routes in my routing table that were learned by the routing protocol from
which routes are being redistributed.
2- Take all connected subnets matched by that routing protocol’s network commands.
The redistribute command includes a subnets option, but only OSPF needs to use it. By
default, when redistributing into OSPF, OSPF redistributes only routes for classful networks, ignoring subnets. By including the subnets option, OSPF redistributes subnets as well.
The other IGPs redistribute subnets automatically, but, if at a network boundary, the RIP or EIGRP auto-summary setting would still cause summarization to use the classful network. If either RIP or EIGRP had used auto-summary, each redistributed network would show just the classful networks.
Cisco IOS provides three mechanisms for setting the metrics of redistributed routes, as
follows:
1- Call a route map from the redistribute command, with the route map using the set
metric command. This method allows different metrics for different routes.
2- Use the metric option on the redistribute command. This sets the same metric for
all routes redistributed by that redistribute command.
3- Use the default-metric command under the router command. This command sets the
metric for all redistributed routes whose metric was not set by either of the other
two methods.
The list implies the order of precedence if more than one method defines a metric. For
example, if a route’s metric is set by all three methods, the route map’s metric is used. If
the metric is set on the redistribute command and there is a default-metric command as
well, the setting on the redistribute command takes precedence.
The redistribute command also allows a setting for the metric-type option, which really
refers to the route type. For example, routes redistributed into OSPF must be OSPF
external routes, but they can be either external type 1 (E1) or type 2 (E2) routes.
Below summarizes the defaults for metrics and metric types.
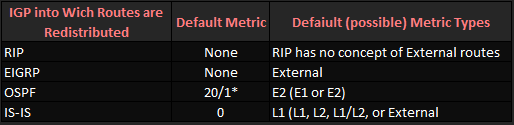
* OSPF uses cost 20 when redistributing from an IGP, and cost 1 when redistributing from BGP.
Mutual Redistribution with Multiple Routers Considerations
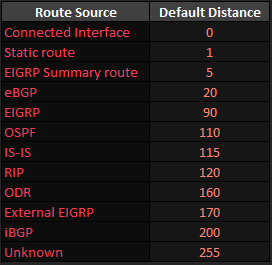
When multiple routers redistribute between the same two routing protocol domains, several potential problems can occur like routing loops. One type of problem occurs on the redistributing routers, because those routers will learn a route to most subnets through both routing protocols.
A router uses the AD to determine the best route when comparing the best routes from each of the two routing protocols, this typically results in some routes using suboptimal paths.
To solve this type of problem, the redistributing routers must have some awareness of
which routes came from the other routing domain. In particular, the lower-AD routing
protocol needs to decide which routes came from the higher-AD routing protocol, and
either use a different AD for those routes or filter the routes.
Preventing Suboptimal Routes by Setting the Administrative Distance
One simple solution to the problem of suboptimal routes on redistributing routers is to flag the redistributed routes with a higher AD. A route’s AD is not advertised by the routing protocol. However, a single router can be configured such that it assigns different AD values to different routes, which then impacts that one router’s choice of which routes end up in that router’s routing table.
For example, a router running redistribution between RIP/OSPF could assign an OSPF-learned route and AD of 180, an AD higher than RIP’s 120, thereby preventing the original problem. Or you can even set the default AD for OSPF external routes to 180 under OSPF process thus identifying RIP’s AD 120 the optimal route. There are several solutions.
EIGRP supports the exact same concept by default, using AD 170 for External routes
and 90 for Internal routes. You can reset EIGRP’s distance for internal and external routes by using the distance eigrp router subcommand.
The distance router subcommand can be used in a different way, influencing some of or all the routes that come from a particular router. The syntax is as follows:
distance {distance-value ip-address {wildcard-mask} [ip-standard-list] [ip-extended-list]
This command sets three key pieces of information:
1- AD to be set.
2- IP address of the router advertising the routes.
3- ACL with which to match routes.
With RIP and EIGRP, this command identifies a neighboring router’s interface address using the ip-address wildcard-mask parameters. With OSPF, those same parameters identify the RID of the router owning (creating) the LSA for the route. The optional ACL then identifies the subset of routes for which the AD will be set. The logic boils down to something like this:
Set this AD value for all routes learned from a router that is defined by the IP
address and wildcard mask, and for which the ACL permits the route.
Preventing Suboptimal Routes by Using Route Tags
Another method of preventing suboptimal routing on the redistributing routers is to simply filter the problematic routes.
Performing simple route filtering based on IP subnet number works, but the redistributing
routers will need to be reconfigured every time subnets change in the higher-AD routing domain. The administrative effort can be improved by adding route tagging to the process.
When you tag all routes taken from the higher-AD domain and advertised into the lower-AD domain, the distribute-list command can make a simple check for that tag.
Route tags are simply unitless integer values in the data structure of a route. These tags,
typically either 16 or 32 bits long depending on the routing protocol, allow a router to
imply something about a route that was redistributed from another routing protocol.
For example, RZ can tag its OSPF-advertised route to 10.1.2.0/24 with a tag—say, 7777. OSPF does not define what a tag of 7777 means, but the OSPF protocol includes the tag field in the LSA so that it can be used for administrative purposes. Later, RY can filter routes based on their tag, solving the suboptimal route problem.
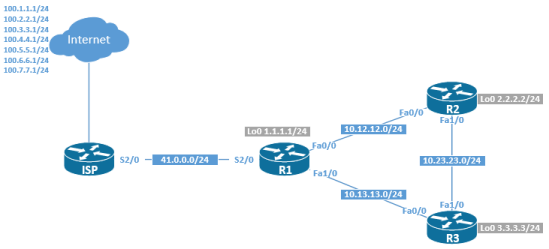
Redistribution Between EIGRP and OSPF Lab
I have built a topology in the previous post about route filtering, which I will be using for this post as well. With EIGRP and OSPF, and I’ll add one more example redistributing between RIPv2 and OSPF, because the behaviour differs from protocol to protocol.
In the first lab, R1 and R2 are running EIGRP AS 1, and R2 and R3 are running OSPF. R2 is the ASBR consisting of areas 0 and 10 and R3 is an ABR running Areas 0 and 20.
Routers are running the following:
R1# sh version
Cisco IOS Software, Linux Software (I86BI_LINUX-ADVENTERPRISEK9-M), Version 15.4(2)T4, DEVELOPMENT TEST SOFTWARE
Technical Support: http://www.cisco.com/techsupport
Copyright (c) 1986-2015 by Cisco Systems, Inc.
Compiled Thu 08-Oct-15 21:21 by prod_rel_team
Topology
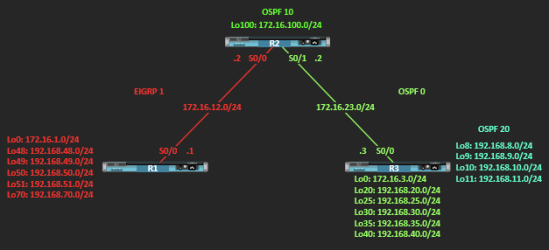
Scenario Objectives
- Review EIGRP and OSPF configuration.
- Summarize routes in EIGRP and OSPF (at the ABR/ASBR).
- Redistribute into EIGRP.
- Redistribute into OSPF.
Initial configuration of all loopback interfaces and serial interfaces with IP addresses and bring them up on all routers.
R1# conf t
Enter configuration commands, one per line. End with CNTL/Z.
R1(config)# int lo0
*May 30 16:00:54.416: %LINEPROTO-5-UPDOWN: Line protocol on Interface Loopback0, changed state to up
R1(config-if)# ip add 172.16.1.1 255.255.255.0
R1(config-if)# int lo48
*May 30 16:01:17.232: %LINEPROTO-5-UPDOWN: Line protocol on Interface Loopback48, changed state to up
R1(config-if)# ip add 192.168.48.1 255.255.255.0
R1(config-if)# int lo49
*May 30 16:01:33.901: %LINEPROTO-5-UPDOWN: Line protocol on Interface Loopback49, changed state to up
R1(config-if)# ip add 192.168.49.1 255.255.255.0
R1(config-if)# int lo50
*May 30 16:01:43.804: %LINEPROTO-5-UPDOWN: Line protocol on Interface Loopback50, changed state to up
R1(config-if)# ip add 192.168.50.1 255.255.255.0
R1(config-if)# int lo51
*May 30 16:01:55.899: %LINEPROTO-5-UPDOWN: Line protocol on Interface Loopback51, changed state to up
R1(config-if)# ip add 192.168.51.1 255.255.255.0
R1(config-if)# int lo70
*May 30 16:02:07.164: %LINEPROTO-5-UPDOWN: Line protocol on Interface Loopback70, changed state to up
R1(config-if)# ip add 192.168.70.1 255.255.255.0
R1(config-if)# int s0/0
R1(config-if)# description TO-R2
R1(config-if)# ip add 172.16.12.1 255.255.255.0
R1(config-if)# clock rate threshold 64000
R1(config-if)# bandwidth 64
R1(config-if)# no shut
*May 30 16:02:58.922: %LINK-3-UPDOWN: Interface Serial0/0, changed state to up
*May 30 16:02:59.924: %LINEPROTO-5-UPDOWN: Line protocol on Interface Serial0/0, changed state to up
*May 30 16:03:21.499: %LINEPROTO-5-UPDOWN: Line protocol on Interface Serial0/0, changed state to down
R1# sh ip int bri | e admin
Interface IP-Address OK? Method Status Protocol
Serial0/0 172.16.12.1 YES manual up up
Loopback0 172.16.1.1 YES manual up up
Loopback48 192.168.48.1 YES manual up up
Loopback49 192.168.49.1 YES manual up up
Loopback50 192.168.50.1 YES manual up up
Loopback51 192.168.51.1 YES manual up up
Loopback70 192.168.70.1 YES manual up up
R1#
R2# conf t
Enter configuration commands, one per line. End with CNTL/Z.
R2(config)# int lo0
*May 30 22:04:11.204: %LINEPROTO-5-UPDOWN: Line protocol on Interface Loopback0, changed state to up
R2(config-if)# ip add 172.16.2.1 255.255.255.0
R2(config)# int lo100
*May 30 19:44:47.464: %LINEPROTO-5-UPDOWN: Line protocol on Interface Loopback100, changed state to up
R2(config-if)# ip add 172.16.100.1 255.255.255.0
R2(config-if)# interface s0/0
R2(config-if)# clock rate threshold 64000
R2(config-if)# bandwidth 64
R2(config-if)# description TO->R1
R2(config-if)# ip add 172.16.12.2 255.255.255.0
R2(config-if)# no shut
*May 30 19:48:10.245: %LINK-3-UPDOWN: Interface Serial0/0, changed state to up
*May 30 19:48:11.247: %LINEPROTO-5-UPDOWN: Line protocol on Interface Serial0/0, changed state to up
R2(config-if)# int s0/1
R2(config-if)# description TO->R3
R2(config-if)# clock rate threshold 64000
R2(config-if)# bandwidth 64
R2(config-if)# ip add 172.16.23.2 255.255.255.0
R2(config-if)# no shut
*May 30 19:49:32.310: %LINK-3-UPDOWN: Interface Serial0/1, changed state to up
*May 30 19:49:33.313: %LINEPROTO-5-UPDOWN: Line protocol on Interface Serial0/1, changed state to up
R2(config-if)# end
R2# sh ip int bri | e admin
Interface IP-Address OK? Method Status Protocol
Serial0/0 172.16.12.2 YES manual up up
Serial0/1 172.16.23.2 YES manual up up
Loopback0 172.16.2.1 YES manual up up
Loopback100 172.16.100.1 YES manual up up
R2#
R3# conf t
Enter configuration commands, one per line. End with CNTL/Z.
R3(config-if)# int lo0
*May 30 21:25:40.301: %LINEPROTO-5-UPDOWN: Line protocol on Interface Loopback0, changed state to up
R3(config-if)# ip add 172.16.3.1 255.255.255.0
R3(config-if)# int lo20
*May 30 21:25:52.609: %LINEPROTO-5-UPDOWN: Line protocol on Interface Loopback20, changed state to up
R3(config-if)# ip add 192.168.20.1 255.255.255.0
R3(config-if)# int lo25
*May 30 21:25:59.826: %LINEPROTO-5-UPDOWN: Line protocol on Interface Loopback25, changed state to up
R3(config-if)# ip add 192.168.25.1 255.255.255.0
R3(config-if)# int lo30
*May 30 21:26:11.917: %LINEPROTO-5-UPDOWN: Line protocol on Interface Loopback30, changed state to up
R3(config-if)# ip add 192.168.30.1 255.255.255.0
R3(config-if)# int lo35
*May 30 21:26:19.254: %LINEPROTO-5-UPDOWN: Line protocol on Interface Loopback35, changed state to up
R3(config-if)# ip add 192.168.35.1 255.255.255.0
R3(config-if)# int lo40
*May 30 21:26:36.641: %LINEPROTO-5-UPDOWN: Line protocol on Interface Loopback40, changed state to up
R3(config-if)# ip add 192.168.40.1 255.255.255.0
R3(config-if)# int lo8
*May 30 19:53:45.050: %LINEPROTO-5-UPDOWN: Line protocol on Interface Loopback8, changed state to up
R3(config-if)# ip add 192.168.8.1 255.255.255.0
R3(config-if)# int lo9
*May 30 19:54:03.868: %LINEPROTO-5-UPDOWN: Line protocol on Interface Loopback9, changed state to up
R3(config-if)# ip add 192.168.9.1 255.255.255.0
R3(config-if)# int lo10
*May 30 19:54:13.650: %LINEPROTO-5-UPDOWN: Line protocol on Interface Loopback10, changed state to up
R3(config-if)# ip add 192.168.10.1 255.255.255.0
R3(config-if)# int lo11
*May 30 19:54:22.250: %LINEPROTO-5-UPDOWN: Line protocol on Interface Loopback11, changed state to up
R3(config-if)# ip add 192.168.11.1 255.255.255.0
R3(config-if)# exit
R3(config)# int s0/1
R3(config-if)# description TO->R2
R3(config-if)# clock rate threshold 64000
R3(config-if)# bandwidth 64
R3(config-if)# ip add 172.16.23.3 255.255.255.0
R3(config-if)# no shut
R3(config-if)# end
*May 30 20:06:54.067: %LINK-3-UPDOWN: Interface Serial0/1, changed state to up
*May 30 20:06:55.067: %LINEPROTO-5-UPDOWN: Line protocol on Interface Serial0/1, changed state to up
R3# sh ip int bri | e admin
Interface IP-Address OK? Method Status Protocol
Serial0/1 172.16.23.3 YES manual up up
Loopback0 172.16.3.1 YES manual up up
Loopback8 192.168.8.1 YES manual up up
Loopback9 192.168.9.1 YES manual up up
Loopback10 192.168.10.1 YES manual up up
Loopback11 192.168.11.1 YES manual up up
Loopback20 192.168.20.1 YES manual up up
Loopback25 192.168.25.1 YES manual up up
Loopback30 192.168.30.1 YES manual up up
Loopback35 192.168.35.1 YES manual up up
Loopback40 192.168.40.1 YES manual up up
R3#
Now configure EIGRP between R1 and R2
R1> en
R1# conf t
Enter configuration commands, one per line. End with CNTL/Z.
R1(config)# router eigrp 1
R1(config-router)# no auto-summary
R1(config-router)# network 172.16.0.0
R1(config-router)# network 192.168.48.0 0.0.255.255
R1(config-router)#
R2> en
R2# conf t
Enter configuration commands, one per line. End with CNTL/Z.
R2(config)# router eigrp 1
R2(config-router)# no auto-summary
R2(config-router)# network 172.16.0.0 0.0.255.255
R2(config-router)#
*Jun 14 18:13:47.355: %DUAL-5-NBRCHANGE: EIGRP-IPv4 1: Neighbor 172.16.12.1 (Serial0/0) is up: new adjacency
R2(config-router)#
Verify EIGRP configuration between R1 and R2.
R1# sh ip eigrp neighbors
EIGRP-IPv4 Neighbors for AS(1)
H Address Interface Hold Uptime SRTT RTO Q Seq
(sec) (ms) Cnt Num
0 172.16.12.2 Se0/0 12 00:02:07 43 2340 0 3
R1# sh ip route eigrp
Codes: L - local, C - connected, S - static, R - RIP, M - mobile, B - BGP
D - EIGRP, EX - EIGRP external, O - OSPF, IA - OSPF inter area
N1 - OSPF NSSA external type 1, N2 - OSPF NSSA external type 2
E1 - OSPF external type 1, E2 - OSPF external type 2
i - IS-IS, su - IS-IS summary, L1 - IS-IS level-1, L2 - IS-IS level-2
ia - IS-IS inter area, * - candidate default, U - per-user static route
o - ODR, P - periodic downloaded static route, H - NHRP, l - LISP
a - application route
+ - replicated route, % - next hop override
Gateway of last resort is not set
172.16.0.0/16 is variably subnetted, 7 subnets, 2 masks
D 172.16.2.0/24 [90/40640000] via 172.16.12.2, 00:00:06, Serial0/0
D 172.16.23.0/24 [90/41024000] via 172.16.12.2, 00:03:30, Serial0/0
D 172.16.100.0/24 [90/40640000] via 172.16.12.2, 00:03:30, Serial0/0
R1#
R2# sh ip eigrp neighbors
EIGRP-IPv4 Neighbors for AS(1)
H Address Interface Hold Uptime SRTT RTO Q Seq
(sec) (ms) Cnt Num
0 172.16.12.1 Se0/0 14 00:08:20 40 2340 0 4
R2# sh ip route eigrp
Codes: L - local, C - connected, S - static, R - RIP, M - mobile, B - BGP
D - EIGRP, EX - EIGRP external, O - OSPF, IA - OSPF inter area
N1 - OSPF NSSA external type 1, N2 - OSPF NSSA external type 2
E1 - OSPF external type 1, E2 - OSPF external type 2
i - IS-IS, su - IS-IS summary, L1 - IS-IS level-1, L2 - IS-IS level-2
ia - IS-IS inter area, * - candidate default, U - per-user static route
o - ODR, P - periodic downloaded static route, H - NHRP, l - LISP
a - application route
+ - replicated route, % - next hop override
Gateway of last resort is not set
172.16.0.0/16 is variably subnetted, 9 subnets, 2 masks
D 172.16.1.0/24 [90/40640000] via 172.16.12.1, 00:08:24, Serial0/0
D 192.168.48.0/24 [90/40640000] via 172.16.12.1, 00:08:24, Serial0/0
D 192.168.49.0/24 [90/40640000] via 172.16.12.1, 00:08:24, Serial0/0
D 192.168.50.0/24 [90/40640000] via 172.16.12.1, 00:08:24, Serial0/0
D 192.168.51.0/24 [90/40640000] via 172.16.12.1, 00:08:24, Serial0/0
D 192.168.70.0/24 [90/40640000] via 172.16.12.1, 00:08:24, Serial0/0
R2#
Now let’s test reachability between R1 and R2, use the script below to simplify the process.
R2# tclsh
R2(tcl)# foreach n {
+>(tcl)# 172.16.1.1
+>(tcl)# 192.168.48.1
+>(tcl)# 192.168.49.1
+>(tcl)# 192.168.50.1
+>(tcl)# 192.168.51.1
+>(tcl)# 192.168.70.1
+>(tcl)# 172.16.12.1
+>(tcl)# 172.16.12.2
+>(tcl)# 172.16.2.1
+>(tcl)# } {ping $n }
Type escape sequence to abort.
Sending 5, 100-byte ICMP Echos to 172.16.1.1, timeout is 2 seconds:
!!!!!
Success rate is 100 percent (5/5), round-trip min/avg/max = 31/33/34 ms
Type escape sequence to abort.
Sending 5, 100-byte ICMP Echos to 192.168.48.1, timeout is 2 seconds:
!!!!!
Success rate is 100 percent (5/5), round-trip min/avg/max = 28/30/33 ms
Type escape sequence to abort.
Sending 5, 100-byte ICMP Echos to 192.168.49.1, timeout is 2 seconds:
!!!!!
Success rate is 100 percent (5/5), round-trip min/avg/max = 30/32/34 ms
Type escape sequence to abort.
Sending 5, 100-byte ICMP Echos to 192.168.50.1, timeout is 2 seconds:
!!!!!
Success rate is 100 percent (5/5), round-trip min/avg/max = 28/32/35 ms
Type escape sequence to abort.
Sending 5, 100-byte ICMP Echos to 192.168.51.1, timeout is 2 seconds:
!!!!!
Success rate is 100 percent (5/5), round-trip min/avg/max = 30/32/34 ms
Type escape sequence to abort.
Sending 5, 100-byte ICMP Echos to 192.168.70.1, timeout is 2 seconds:
!!!!!
Success rate is 100 percent (5/5), round-trip min/avg/max = 33/33/34 ms
Type escape sequence to abort.
Sending 5, 100-byte ICMP Echos to 172.16.12.1, timeout is 2 seconds:
!!!!!
Success rate is 100 percent (5/5), round-trip min/avg/max = 31/32/34 ms
Type escape sequence to abort.
Sending 5, 100-byte ICMP Echos to 172.16.12.2, timeout is 2 seconds:
!!!!!
Success rate is 100 percent (5/5), round-trip min/avg/max = 66/66/66 ms
Type escape sequence to abort.
Sending 5, 100-byte ICMP Echos to 172.16.2.1, timeout is 2 seconds:
!!!!!
Success rate is 100 percent (5/5), round-trip min/avg/max = 4/4/5 ms
R2(tcl)#
Manually Summarize with EIGRP
To make routing updates more efficient and ultimately reduce the size of the routing table, contiguous EIGRP routes can be summarized out an interface by using the ip summary-address eigrp interface configuration command.
R1# conf t
Enter configuration commands, one per line. End with CNTL/Z.
R1(config)# interface s0/0
R1(config-if)# ip summary-address eigrp 1 192.168.48.0 255.255.254.0
R1(config-if)#
*Jun 14 19:09:33.343: %DUAL-5-NBRCHANGE: EIGRP-IPv4 1: Neighbor 172.16.12.2 (Serial0/0) is resync: summary configured
R1(config-if)# end
R1# sh ip route eigrp | b Gateway
Gateway of last resort is not set
172.16.0.0/16 is variably subnetted, 7 subnets, 2 masks
D 172.16.2.0/24 [90/40640000] via 172.16.12.2, 00:55:45, Serial0/0
D 172.16.23.0/24 [90/41024000] via 172.16.12.2, 00:59:09, Serial0/0
D 172.16.100.0/24 [90/40640000] via 172.16.12.2, 00:59:09, Serial0/0
D 192.168.48.0/23 is a summary, 00:03:23, Null0
R1#
Verify the summarized routes in detail. Notice that the route is pointing to Null0.
R1# sh ip route 192.168.48.0 255.255.254.0
Routing entry for 192.168.48.0/23, supernet
Known via "eigrp 1", distance 5, metric 128256, type internal
Redistributing via eigrp 1
Routing Descriptor Blocks:
* directly connected, via Null0
Route metric is 128256, traffic share count is 1
Total delay is 5000 microseconds, minimum bandwidth is 8000000 Kbit
Reliability 255/255, minimum MTU 1514 bytes
Loading 1/255, Hops 0
R1#
A summary address route has an AD of 5, so it will be prefered when a device looks for a route belonging to that summary range. The fact that the route points to interface Null0 is a loop prevention mechanism. What it does is silently drops traffic requesting routes within the summary address range but are not advertised by the router or not present on the routing table. In other words, a route might not exist in the routing table but still be within the summary address range. When this occurs, traffic is silently dropped as a loop prevention mechanism.
Now let’s verify the routing table on R2. Note that the summary address is in the table.
R2> sh ip route eigrp | b Gateway
Gateway of last resort is not set
172.16.0.0/16 is variably subnetted, 9 subnets, 2 masks
D 172.16.1.0/24 [90/40640000] via 172.16.12.1, 03:04:49, Serial0/0
D 192.168.48.0/23 [90/40640000] via 172.16.12.1, 00:00:26, Serial0/0
D 192.168.50.0/24 [90/40640000] via 172.16.12.1, 03:04:49, Serial0/0
D 192.168.51.0/24 [90/40640000] via 172.16.12.1, 03:04:49, Serial0/0
D 192.168.70.0/24 [90/40640000] via 172.16.12.1, 03:04:49, Serial0/0
R2>
Now, because we configured EIGRP with one statement covering the 172.16.0.0/16 range, all interfaces configured with any address in that same range are participating in EIGRP. In the case of R1 it does not have negative affect as R1 only connects to R2 running EIGRP. Let’s take a look.
R2# sh ip eigrp interfaces
EIGRP-IPv4 Interfaces for AS(1)
Xmit Queue PeerQ Mean Pacing Time Multicast Pending
Interface Peers Un/Reliable Un/Reliable SRTT Un/Reliable Flow Timer Routes
Se0/0 1 0/0 0/0 44 10/390 546 0
Se0/1 0 0/0 0/0 0 10/10 0 0
Lo0 0 0/0 0/0 0 0/0 0 0
Lo100 0 0/0 0/0 0 0/0 0 0
R2#
The serial interface s0/1 connected to R3 is sending and receiving EIGRP packets but it’s supposed to process only OSPF packets and exchange neighbor information with R3. Let’s prevent R2 from processing EIGRP packets on the serial link connected to R3.
R2# conf t
Enter configuration commands, one per line. End with CNTL/Z.
R2(config)# router eigrp 1
R2(config-router)# passive-interface s0/1
R2(config-router)# end
R2#
R2# sh ip protocols
*** IP Routing is NSF aware ***
Routing Protocol is "eigrp 1"
<output omitted>
Automatic Summarization: disabled
Maximum path: 4
Routing for Networks:
172.16.0.0
Passive Interface(s):
Serial0/1
Routing Information Sources:
Gateway Distance Last Update
172.16.12.1 90 00:01:24
Distance: internal 90 external 170
That’s more like it! We now have only s0/0 interface connected to R1 running and processing EIGRP packets. Alrighty then!
Configure OSPF on and between R2 and R3
Now let’s configure R3 and R2 to run OSPF, beginning on R3.
R3# conf t
Enter configuration commands, one per line. End with CNTL/Z.
R3(config)# router ospf 1
R3(config-router)# network 172.16.3.1 0.0.0.0 area 0
R3(config-router)# network 172.16.23.3 0.0.0.0 area 0
R3(config-router)# network 192.168.8.0 0.0.3.255 area 20
R3(config-router)# network 192.168.20.1 0.0.0.0 area 0
R3(config-router)# network 192.168.25.1 0.0.0.0 area 0
R3(config-router)# network 192.168.30.1 0.0.0.0 area 0
R3(config-router)# network 192.168.35.1 0.0.0.0 area 0
R3(config-router)# network 192.168.40.1 0.0.0.0 area 0
R3(config-router)#
R2# conf t
Enter configuration commands, one per line. End with CNTL/Z.
R2(config)# router ospf 1
R2(config-router)# network 172.16.23.0 0.0.0.255 area 0
R2(config-router)# network 172.16.100.0 0.0.0.255 area 10
R2(config-router)#
*Jun 15 04:19:01.385: %OSPF-5-ADJCHG: Process 1, Nbr 192.168.40.1 on Serial0/1 from LOADING to FULL, Loading Done
R2(config-router)#
Verify that your adjacencies come up and make sure that you have routes from OSPF populating the R2 routing table.
R2# sh ip ospf neighbor
Neighbor ID Pri State Dead Time Address Interface
192.168.40.1 0 FULL/ - 00:00:35 172.16.23.3 Serial0/1
R2#
R3# sh ip ospf neighbor
Neighbor ID Pri State Dead Time Address Interface
172.16.100.1 0 FULL/ - 00:00:31 172.16.23.2 Serial0/1
R3#
R2# show ip route ospf | b Gateway
Gateway of last resort is not set
172.16.0.0/16 is variably subnetted, 10 subnets, 2 masks
O 172.16.3.0/24 [110/1563] via 172.16.23.3, 00:08:26, Serial0/1
O IA 192.168.8.0/24 [110/1563] via 172.16.23.3, 00:08:26, Serial0/1
O IA 192.168.9.0/24 [110/1563] via 172.16.23.3, 00:08:26, Serial0/1
O IA 192.168.10.0/24 [110/1563] via 172.16.23.3, 00:08:26, Serial0/1
O IA 192.168.11.0/24 [110/1563] via 172.16.23.3, 00:08:26, Serial0/1
O 192.168.20.0/24 [110/1563] via 172.16.23.3, 00:08:26, Serial0/1
O 192.168.25.0/24 [110/1563] via 172.16.23.3, 00:08:26, Serial0/1
O 192.168.30.0/24 [110/1563] via 172.16.23.3, 00:08:26, Serial0/1
O 192.168.35.0/24 [110/1563] via 172.16.23.3, 00:08:26, Serial0/1
O 192.168.40.0/24 [110/1563] via 172.16.23.3, 00:08:26, Serial0/1
R2#
We’re good to go!
Summarize OSPF Areas at the ABR
Now let’s review the R2 routing table, and notice the Inter-area routes being advertised from R3 loopbacks in area 20. We can do a better job advertizing all these routes.
R2# show ip route ospf | b Gateway
Gateway of last resort is not set
172.16.0.0/16 is variably subnetted, 10 subnets, 2 masks
O 172.16.3.0/24 [110/1563] via 172.16.23.3, 00:08:26, Serial0/1
O IA 192.168.8.0/24 [110/1563] via 172.16.23.3, 00:08:26, Serial0/1
O IA 192.168.9.0/24 [110/1563] via 172.16.23.3, 00:08:26, Serial0/1
O IA 192.168.10.0/24 [110/1563] via 172.16.23.3, 00:08:26, Serial0/1
O IA 192.168.11.0/24 [110/1563] via 172.16.23.3, 00:08:26, Serial0/1
O 192.168.20.0/24 [110/1563] via 172.16.23.3, 00:08:26, Serial0/1
O 192.168.25.0/24 [110/1563] via 172.16.23.3, 00:08:26, Serial0/1
O 192.168.30.0/24 [110/1563] via 172.16.23.3, 00:08:26, Serial0/1
O 192.168.35.0/24 [110/1563] via 172.16.23.3, 00:08:26, Serial0/1
O 192.168.40.0/24 [110/1563] via 172.16.23.3, 00:08:26, Serial0/1
R2#
Let’s summarize the routes from area 20 into a single Inter-area route on R3. This way, we can have a nice and tidy routing table which not only can be better analyzed but also helps on resources.
R3# conf t
Enter configuration commands, one per line. End with CNTL/Z.
R3(config)# router ospf 1
R3(config-router)# area 20 range 192.168.8.0 255.255.252.0
R3(config-router)#
Verify on R2 that you are now receiving the summarized route from R3.
R2# show ip route ospf | b Gateway
Gateway of last resort is not set
172.16.0.0/16 is variably subnetted, 10 subnets, 2 masks
O 172.16.3.0/24 [110/1563] via 172.16.23.3, 00:17:59, Serial0/1
O IA 192.168.8.0/22 [110/1563] via 172.16.23.3, 00:00:26, Serial0/1
O 192.168.20.0/24 [110/1563] via 172.16.23.3, 00:17:59, Serial0/1
O 192.168.25.0/24 [110/1563] via 172.16.23.3, 00:17:59, Serial0/1
O 192.168.30.0/24 [110/1563] via 172.16.23.3, 00:17:59, Serial0/1
O 192.168.35.0/24 [110/1563] via 172.16.23.3, 00:17:59, Serial0/1
O 192.168.40.0/24 [110/1563] via 172.16.23.3, 00:17:59, Serial0/1
R2#
Configure mutual redistribution between OSPF and EIGRP
Now let’s configure redistribution between both routing protocols. R2 is the ASBR for the OSPF domain and EIGRP AS, so it will be the key point for redistribution.
The subnets command is necessary because, by default, OSPF only redistributes classful networks and supernets. A default seed metric is not required for OSPF. Under the EIGRP process, we need to tell EIGRP to redistribute OSPF process 1 with specific metrics: bandwidth of 10000, delay of 100, reliability of 255/255, load of 1/255, and a MTU of 1500. Like RIP, EIGRP requires a seed metric. You can also set a default seed metric with the default-metric command.
R2# conf t
Enter configuration commands, one per line. End with CNTL/Z.
R2(config)# router ospf 1
R2(config-router)# redistribute eigrp 1 subnets
R2(config-router)# exit
R2(config)# router eigrp 1
R2(config-router)# redistribute ospf 1 metric 10000 100 255 1 1500
R2(config-router)#
We could also define a default seed metric and just redistribute the OSPF process. Both of the commands work the same way.
R2(config-router)# default-metric 10000 100 255 1 1500
R2(config-router)# redistribute ospf 1
Now let’s verify the change on the redistributing router R2.
R2# sh ip protocols
*** IP Routing is NSF aware ***
Routing Protocol is "application"
Sending updates every 0 seconds
Invalid after 0 seconds, hold down 0, flushed after 0
Outgoing update filter list for all interfaces is not set
Incoming update filter list for all interfaces is not set
Maximum path: 32
Routing for Networks:
Routing Information Sources:
Gateway Distance Last Update
Distance: (default is 4)
Routing Protocol is "eigrp 1"
Outgoing update filter list for all interfaces is not set
Incoming update filter list for all interfaces is not set
Default networks flagged in outgoing updates
Default networks accepted from incoming updates
Redistributing: ospf 1
EIGRP-IPv4 Protocol for AS(1)
Metric weight K1=1, K2=0, K3=1, K4=0, K5=0
NSF-aware route hold timer is 240
Router-ID: 172.16.100.1
Topology : 0 (base)
Active Timer: 3 min
Distance: internal 90 external 170
Maximum path: 4
Maximum hopcount 100
Maximum metric variance 1
Automatic Summarization: disabled
Maximum path: 4
Routing for Networks:
172.16.0.0
Passive Interface(s):
Serial0/1
Routing Information Sources:
Gateway Distance Last Update
172.16.12.1 90 00:56:10
Distance: internal 90 external 170
Routing Protocol is "ospf 1"
Outgoing update filter list for all interfaces is not set
Incoming update filter list for all interfaces is not set
Router ID 172.16.100.1
It is an area border and autonomous system boundary router
Redistributing External Routes from,
eigrp 1, includes subnets in redistribution
Number of areas in this router is 2. 2 normal 0 stub 0 nssa
Maximum path: 4
Routing for Networks:
172.16.23.0 0.0.0.255 area 0
172.16.100.0 0.0.0.255 area 10
Routing Information Sources:
Gateway Distance Last Update
192.168.40.1 110 00:38:28
Distance: (default is 110)
R2#
Now let’s verify the routing tables on R1 and R3 so that we can see the redistributed routes. Redistributed OSPF routes display on R1 as D EX, (External EIGRP routes – AD 170). Redistributed EIGRP routes are tagged in R3’s routing table as O E2, (OSPF External Type 2, which do not increment their metric as they traverse the path). Type 2 is the default OSPF External Type.
R1> sh ip route eigrp | b Gateway
Gateway of last resort is not set
172.16.0.0/16 is variably subnetted, 8 subnets, 2 masks
D 172.16.2.0/24 [90/40640000] via 172.16.12.2, 01:13:39, Serial0/0
D EX 172.16.3.0/24 [170/40537600] via 172.16.12.2, 00:09:59, Serial0/0
D 172.16.23.0/24 [90/41024000] via 172.16.12.2, 01:13:39, Serial0/0
D 172.16.100.0/24 [90/40640000] via 172.16.12.2, 01:13:39, Serial0/0
D EX 192.168.8.0/22 [170/40537600] via 172.16.12.2, 00:09:59, Serial0/0
D EX 192.168.20.0/24 [170/40537600] via 172.16.12.2, 00:09:59, Serial0/0
D EX 192.168.25.0/24 [170/40537600] via 172.16.12.2, 00:09:59, Serial0/0
D EX 192.168.30.0/24 [170/40537600] via 172.16.12.2, 00:09:59, Serial0/0
D EX 192.168.35.0/24 [170/40537600] via 172.16.12.2, 00:09:59, Serial0/0
D EX 192.168.40.0/24 [170/40537600] via 172.16.12.2, 00:09:59, Serial0/0
D 192.168.48.0/23 is a summary, 01:47:52, Null0
R1>
R3> sh ip route ospf | b Gateway
Gateway of last resort is not set
172.16.0.0/16 is variably subnetted, 8 subnets, 2 masks
O E2 172.16.1.0/24 [110/20] via 172.16.23.2, 00:13:39, Serial0/1
O E2 172.16.2.0/24 [110/20] via 172.16.23.2, 00:13:39, Serial0/1
O E2 172.16.12.0/24 [110/20] via 172.16.23.2, 00:13:39, Serial0/1
O IA 172.16.100.0/24 [110/1563] via 172.16.23.2, 00:45:51, Serial0/1
O 192.168.8.0/22 is a summary, 00:45:51, Null0
O E2 192.168.48.0/23 [110/20] via 172.16.23.2, 00:13:39, Serial0/1
O E2 192.168.50.0/24 [110/20] via 172.16.23.2, 00:13:39, Serial0/1
O E2 192.168.51.0/24 [110/20] via 172.16.23.2, 00:13:39, Serial0/1
O E2 192.168.70.0/24 [110/20] via 172.16.23.2, 00:13:39, Serial0/1
R3>
Now, let’s verify full reachability between all segments on both R1 and R3. I’m not putting the output of the echo replies, kinda too long but it’s working, nothing is missing on my side.
R1# tclsh
R1(tcl)#foreach n {
+>(tcl)#172.16.1.1
+>(tcl)#192.168.48.1
+>(tcl)#192.168.49.1
+>(tcl)#192.168.50.1
+>(tcl)#192.168.51.1
+>(tcl)#192.168.70.1
+>(tcl)#172.16.12.1
+>(tcl)#172.16.12.2
+>(tcl)#172.16.2.1
+>(tcl)#172.16.100.1
+>(tcl)#172.16.23.2
+>(tcl)#172.16.23.3
+>(tcl)#172.16.3.1
+>(tcl)#192.168.8.1
+>(tcl)#192.168.9.1
+>(tcl)#192.168.10.1
+>(tcl)#192.168.11.1
+>(tcl)#192.168.20.1
+>(tcl)#192.168.25.1
+>(tcl)#192.168.30.1
+>(tcl)#192.168.35.1
+>(tcl)#192.168.40.1
+>(tcl)# } {ping $n }
Summarize external routes into OSPF at the ASBR
Now let’s summarize those EIGRP routes that R1 is advertising as a summary address range onR2, the ASBR for OSPF domain, but first let’s look at R3’s routing table.
R3> sh ip route ospf | b Gateway
Gateway of last resort is not set
172.16.0.0/16 is variably subnetted, 8 subnets, 2 masks
O E2 172.16.1.0/24 [110/20] via 172.16.23.2, 00:32:36, Serial0/1
O E2 172.16.2.0/24 [110/20] via 172.16.23.2, 00:32:36, Serial0/1
O E2 172.16.12.0/24 [110/20] via 172.16.23.2, 00:32:36, Serial0/1
O IA 172.16.100.0/24 [110/1563] via 172.16.23.2, 01:04:48, Serial0/1
O 192.168.8.0/22 is a summary, 01:04:48, Null0
O E2 192.168.48.0/23 [110/20] via 172.16.23.2, 00:32:36, Serial0/1
O E2 192.168.50.0/24 [110/20] via 172.16.23.2, 00:32:36, Serial0/1
O E2 192.168.51.0/24 [110/20] via 172.16.23.2, 00:32:36, Serial0/1
O E2 192.168.70.0/24 [110/20] via 172.16.23.2, 00:32:36, Serial0/1
R3>
We are receiving the 192.168.48.0/23 summary configured on R1 and advertised by EIGRP, which is being redistributed from R2, but, we are still receiving the individual routes that belong to that summary address. Let’s fix it by configuring a supernet on R2 and prevent the individual routes from being advertised.
R2# conf t
Enter configuration commands, one per line. End with CNTL/Z.
R2(config)# router ospf 1
R2(config-router)# summary-address 192.168.48.0 255.255.252.0
R2(config-router)#
R3> sh ip route ospf | b Gateway
Gateway of last resort is not set
172.16.0.0/16 is variably subnetted, 8 subnets, 2 masks
O E2 172.16.1.0/24 [110/20] via 172.16.23.2, 00:36:57, Serial0/1
O E2 172.16.2.0/24 [110/20] via 172.16.23.2, 00:36:57, Serial0/1
O E2 172.16.12.0/24 [110/20] via 172.16.23.2, 00:36:57, Serial0/1
O IA 172.16.100.0/24 [110/1563] via 172.16.23.2, 01:09:09, Serial0/1
O 192.168.8.0/22 is a summary, 01:09:09, Null0
O E2 192.168.48.0/22 [110/20] via 172.16.23.2, 00:00:01, Serial0/1
O E2 192.168.70.0/24 [110/20] via 172.16.23.2, 00:36:57, Serial0/1
R3>
That looks a lot better.
Redistribution between RIPv2 and OSPF
Now let’s clear the EIGRP configuration and replace it with RIPv2. Perform the redistribution but this time between OSPF and RIPv2.
Objectives
• Review configuration and verification of RIP and OSPF.
• Configure passive interfaces in both RIP and OSPF.
• Filter routing updates using distribute lists.
• Redistribute static routes into RIP.
• Redistribute RIP routes into OSPF.
• Redistribute OSPF routes into RIP.
• Originate a default route into OSPF.
• Set a default seed metric.
• Modify OSPF external network types.
• Configure summary addresses.
Let’s begin on R1 and then R2.
R1# conf t
R1(config)# no router eigrp 1
R1(config)# router rip
R1(config-router)# version 2
R1(config-router)# no auto-summary
R1(config-router)# network 172.16.0.0
R1(config-router)# network 192.168.48.0
R1(config-router)# network 192.168.49.0
R1(config-router)# network 192.168.50.0
R1(config-router)# network 192.168.51.0
R1(config-router)# network 192.168.70.0
R2# conf t
Enter configuration commands, one per line. End with CNTL/Z.
R2(config)# no router eigrp 1
R2(config)# router ospf 1
R2(config-router)# no summary-address 192.168.48.0 255.255.252.0
R2(config-router)# router rip
R2(config-router)# version 2
R2(config-router)# no auto-summary
R2(config-router)# network 172.16.0.0
R2(config-router)#
Let’s verify that the RIP routes were learned from both routers. Also, let’s verify which routes are coming in from RIP advertisements.
R2# sh ip route rip | b Gateway
Gateway of last resort is not set
172.16.0.0/16 is variably subnetted, 10 subnets, 2 masks
R 172.16.1.0/24 [120/1] via 172.16.12.1, 00:00:19, Serial0/0
R 192.168.48.0/24 [120/1] via 172.16.12.1, 00:00:19, Serial0/0
R 192.168.49.0/24 [120/1] via 172.16.12.1, 00:00:19, Serial0/0
R 192.168.50.0/24 [120/1] via 172.16.12.1, 00:00:19, Serial0/0
R 192.168.51.0/24 [120/1] via 172.16.12.1, 00:00:19, Serial0/0
R 192.168.70.0/24 [120/1] via 172.16.12.1, 00:00:19, Serial0/0
R2# sh ip rip database
172.16.0.0/16 auto-summary
172.16.1.0/24
[1] via 172.16.12.1, 00:00:04, Serial0/0
172.16.2.0/24 directly connected, Loopback0
172.16.12.0/24 directly connected, Serial0/0
172.16.23.0/24 directly connected, Serial0/1
172.16.100.0/24 directly connected, Loopback100
192.168.48.0/24 auto-summary
192.168.48.0/24
[1] via 172.16.12.1, 00:00:04, Serial0/0
192.168.49.0/24 auto-summary
192.168.49.0/24
[1] via 172.16.12.1, 00:00:04, Serial0/0
192.168.50.0/24 auto-summary
192.168.50.0/24
[1] via 172.16.12.1, 00:00:04, Serial0/0
192.168.51.0/24 auto-summary
192.168.51.0/24
[1] via 172.16.12.1, 00:00:04, Serial0/0
192.168.70.0/24 auto-summary
192.168.70.0/24
[1] via 172.16.12.1, 00:00:04, Serial0/0
R2#
R1# sh ip route rip | b Gateway
Gateway of last resort is not set
172.16.0.0/16 is variably subnetted, 7 subnets, 2 masks
R 172.16.2.0/24 [120/1] via 172.16.12.2, 00:00:24, Serial0/0
R 172.16.23.0/24 [120/1] via 172.16.12.2, 00:00:24, Serial0/0
R 172.16.100.0/24 [120/1] via 172.16.12.2, 00:00:24, Serial0/0
R1# sh ip rip database
172.16.0.0/16 auto-summary
172.16.1.0/24 directly connected, Loopback0
172.16.2.0/24
[1] via 172.16.12.2, 00:00:17, Serial0/0
172.16.12.0/24 directly connected, Serial0/0
172.16.23.0/24
[1] via 172.16.12.2, 00:00:17, Serial0/0
172.16.100.0/24
[1] via 172.16.12.2, 00:00:17, Serial0/0
192.168.48.0/24 auto-summary
192.168.48.0/24 directly connected, Loopback48
192.168.49.0/24 auto-summary
192.168.49.0/24 directly connected, Loopback49
192.168.50.0/24 auto-summary
192.168.50.0/24 directly connected, Loopback50
192.168.51.0/24 auto-summary
192.168.51.0/24 directly connected, Loopback51
192.168.70.0/24 auto-summary
192.168.70.0/24 directly connected, Loopback70
R1#
Just by looking at it its easy to see that this is not properly configured, to begin with, the segments 172.16.23.0/24 and 172.16.100.0/24 are being advertised by OSPF. Let’s use the passive interfaces on R2 and observe RIP’s behaviour, also check R1’s routing table.
R2# conf t
Enter configuration commands, one per line. End with CNTL/Z.
R2(config)# router rip
R2(config-router)# passive-interface default
R2(config-router)# no passive-interface Serial0/0
R2(config-router)#
R1# sh ip route rip | b Gateway
Gateway of last resort is not set
172.16.0.0/16 is variably subnetted, 7 subnets, 2 masks
R 172.16.2.0/24 [120/1] via 172.16.12.2, 00:00:11, Serial0/0
R 172.16.23.0/24 [120/1] via 172.16.12.2, 00:00:11, Serial0/0
R 172.16.100.0/24 [120/1] via 172.16.12.2, 00:00:11, Serial0/0
R1#
R2’s segments being advertised by OSPF are still being advertised by RIP even after we issued the passive interfaces command and specifically configure only s0/0 interface as being part of RIP. Making an interface in RIP passive only disables updates from being sent through RIP. It does not affect routes being received through it as RIP advertises at classful boundaries.
Also note that when running RIPv2 (not sure why you would want to do that but…), implement passive interfaces as a common practice to save CPU processor cycles and bandwidth on interfaces that do not have to multicast to RIPv2 neighbors. (You can do this on Loopback interfaces also as no neighbor is expected to send/receive updates).
Summarize a supernet with RIP
Let’s configure a supernet summarizing those segments from R1. Note that, In preparing for redistribution, you want to redistribute the minimum number of destination prefixes possible into each of the routing protocols.
Under normal circumstances, you could simply summarize the four consecutive class-C networks with the ip summary address rip command on the R1 serial 0/0 interface.
However, as mentioned above, RIP implementation in Cisco IOS does not allow summarizing to a mask length that is less than the classful network prefix (in this case, 24 bits). This limitation does not affect other routing protocols. For the purpose of the example here, I’m configuring it below and received the following error message:
R1# conf t
Enter configuration commands, one per line. End with CNTL/Z.
R1(config)# interface s0/0
R1(config-if)# ip summary-address rip 192.168.48.0 255.255.252.0
Summary mask must be greater or equal to major net
R1(config-if)#
The solution here with RIP, is to turn it around. Remember from the previous EIGRP lab that summary routes display in the summarizing device’s routing table as having the next hop being the Null0 interface.
We can create an entry manually by using a static route pointing to Null0 and redistribute it into RIP, thereby emulating the approach of EIGRP to a certain extent.
R1(config)# ip route 192.168.48.0 255.255.252.0 null0
R1(config)# router rip
R1(config-router)# redistribute static
R1(config-router)# end
R1#
*Jun 15 09:44:18.465: %SYS-5-CONFIG_I: Configured from console by console
R1#
R1# sh ip route | e L|C
D - EIGRP, EX - EIGRP external, O - OSPF, IA - OSPF inter area
N1 - OSPF NSSA external type 1, N2 - OSPF NSSA external type 2
E1 - OSPF external type 1, E2 - OSPF external type 2
ia - IS-IS inter area, * - candidate default, U - per-user static route
a - application route
+ - replicated route, % - next hop override
Gateway of last resort is not set
172.16.0.0/16 is variably subnetted, 7 subnets, 2 masks
R 172.16.2.0/24 [120/1] via 172.16.12.2, 00:00:03, Serial0/0
R 172.16.23.0/24 [120/1] via 172.16.12.2, 00:00:03, Serial0/0
R 172.16.100.0/24 [120/1] via 172.16.12.2, 00:00:03, Serial0/0
S 192.168.48.0/22 is directly connected, Null0
192.168.48.0/24 is variably subnetted, 2 subnets, 2 masks
192.168.49.0/24 is variably subnetted, 2 subnets, 2 masks
192.168.50.0/24 is variably subnetted, 2 subnets, 2 masks
192.168.51.0/24 is variably subnetted, 2 subnets, 2 masks
192.168.70.0/24 is variably subnetted, 2 subnets, 2 masks
R1#
Note: For RIPv2, it resembles many effects of summarization as performed in other routing protocols like EIGRP or OSPF. Bare in mind, this is not a limitation of RIPv2, but rather a Cisco IOS implementation issue.
On R2, verify that the RIP supernet has been added to the routing table.
R2> sh ip route rip | b Gateway
Gateway of last resort is not set
172.16.0.0/16 is variably subnetted, 10 subnets, 2 masks
R 172.16.1.0/24 [120/1] via 172.16.12.1, 00:00:19, Serial0/0
R 192.168.48.0/22 [120/1] via 172.16.12.1, 00:00:19, Serial0/0
R 192.168.48.0/24 [120/1] via 172.16.12.1, 00:00:19, Serial0/0
R 192.168.49.0/24 [120/1] via 172.16.12.1, 00:00:19, Serial0/0
R 192.168.50.0/24 [120/1] via 172.16.12.1, 00:00:19, Serial0/0
R 192.168.51.0/24 [120/1] via 172.16.12.1, 00:00:19, Serial0/0
R 192.168.70.0/24 [120/1] via 172.16.12.1, 00:00:19, Serial0/0
R2>
And sure enough we are advertising the supernet from R1 but R2 is still receiving each individual route belonging to that summarized range. Just for an example on how to configure on RIP, I’m going to perform some route filtering.
Route Filtering with RIPv2
If you need to advertise certain networks out a particular interface, or you might want to filter updates as they come in, this is possible with distance-vector routing protocols, such as RIP or EIGRP. However, link-state protocols are less flexible, because every router in an area is required to have a synchronized database as a condition for full adjacency.
Distribute lists can be used with either access lists or prefix lists to filter routes by network address. With prefix lists, they can also be configured to filter routes by subnet masks.
In this scenario, you want to filter updates from R1 to R2, allowing only the networks of Loopback 0 and Loopback 70 and the summary route to be advertised.
You want to suppress the more specific prefixes so that routing tables are kept small, and CPU processor cycles on the routers are not wasted.
The 22-bit summary and the 24-bit major network address both have the same address, so access lists will not accomplish the filtering correctly. Therefore, it is necessary to use prefix lists.
In my previous post on Route Filtering, I covered ACLs, Prefix Lists, Route Maps and Distribute Lists in depth. Remember, the ge keyword represents the “greater than or equal to” operator. The le keyword represents the “less than or equal to” operator. If both the ge and le keywords are omitted, the prefix list is processed using an exact match.
On R1, use a prefix list as a distribution filter to prevent the more specific routes from loopbacks 48 through 51 from being advertised. Allow all other destination networks, including the summary route.
R1> en
R1# conf t
Enter configuration commands, one per line. End with CNTL/Z.
R1(config)# ip prefix-list RIP-OUT permit 192.168.48.0/22
R1(config)# ip prefix-list RIP-OUT deny 192.168.48.0/22 le 24
R1(config)# ip prefix-list RIP-OUT permit 0.0.0.0/0 le 32
R1(config)#
Let’s analyze what we just configured. Line 1 of the prefix list permits the summary route and nothing else, because no other route can match that network address with a mask of exactly 22 bits. Line 2 denies all prefixes with a network address in the 192.168.48.0/22 block of addresses that have subnet masks from 22 bits to 24 bits. This removes exactly four network addresses matching the 22, 23, and 24 bits in length of the subnet mask.
Line 2 would deny the 192.168.48.0/22 summary route we created if Line 1 did not explicitly permit the summary route. Line 3 allows all IPv4 prefixes that are not explicitly denied in previous statements of the prefix list.
From the RIP configuration process on R1, apply this prefix list with a distribute-list. Verify R2 routing table afterwards.
R1(config)# router rip
R1(config-router)# distribute-list prefix RIP-OUT out s0/0
R1(config-router)# do sh ip prefix-list
ip prefix-list RIP-OUT: 3 entries
seq 5 permit 192.168.48.0/22
seq 10 deny 192.168.48.0/22 le 24
seq 15 permit 0.0.0.0/0 le 32
R1(config-router)#
R2# clear ip route *
R2# sh ip route rip | b Gateway
Gateway of last resort is not set
172.16.0.0/16 is variably subnetted, 10 subnets, 2 masks
R 172.16.1.0/24 [120/1] via 172.16.12.1, 00:00:06, Serial0/0
R 192.168.48.0/22 [120/1] via 172.16.12.1, 00:00:06, Serial0/0
R 192.168.70.0/24 [120/1] via 172.16.12.1, 00:00:06, Serial0/0
R2# sh ip rip database
172.16.0.0/16 auto-summary
172.16.1.0/24
[1] via 172.16.12.1, 00:00:05, Serial0/0
172.16.2.0/24 directly connected, Loopback0
172.16.12.0/24 directly connected, Serial0/0
172.16.23.0/24 directly connected, Serial0/1
172.16.100.0/24 directly connected, Loopback100
192.168.48.0/22
[1] via 172.16.12.1, 00:00:05, Serial0/0
192.168.70.0/24 auto-summary
192.168.70.0/24
[1] via 172.16.12.1, 00:00:05, Serial0/0
R2#
Note: This could have been achieved by using the out rip syntax instead of the out s0/0. This would allow only the selected prefixes to leave RIP updates. Both accomplish the same goal.
Just for fun, let’s configure that 172.16.23.0/24 segment from being advertised on RIP. Afterall, it belongs to the OSPF process between R2 and R3. I’m also using a prefix list to achieve this goal. First let’s analyze R1’s routing table.
R1# sh ip route rip | b Gateway
Gateway of last resort is not set
172.16.0.0/16 is variably subnetted, 7 subnets, 2 masks
R 172.16.2.0/24 [120/1] via 172.16.12.2, 00:00:37, Serial0/0
R 172.16.23.0/24 [120/1] via 172.16.12.2, 00:00:37, Serial0/0
R 172.16.100.0/24 [120/1] via 172.16.12.2, 00:00:37, Serial0/0
R1#
Alrighty then! Let’s filter that route and verify the result on R1’s routing table.
R2# conf t
Enter configuration commands, one per line. End with CNTL/Z.
R2(config)# ip prefix-list FILTER_172.23_->rip deny 172.16.23.0/24
R2(config)# ip prefix-list FILTER_172.23_->rip permit 0.0.0.0/0 le 32
R2(config)# router rip
R2(config-router)# distribute-list prefix FILTER_172.23_->rip out s0/0
R2(config-router)# end
R2#
R1# sh ip route rip | b Gateway
Gateway of last resort is not set
172.16.0.0/16 is variably subnetted, 6 subnets, 2 masks
R 172.16.2.0/24 [120/1] via 172.16.12.2, 00:00:03, Serial0/0
R 172.16.100.0/24 [120/1] via 172.16.12.2, 00:00:03, Serial0/0
R1# sh ip route 172.16.23.0 255.255.255.0
% Subnet not in table
R1#
And there it is, the segment was filtered!
Now, let’s make a slight configuration change with a single-area OSPF between R2 and R3. On R2, include just the s0/1 link connecting to R3 (the segment we just filtered out of RIP advertisements. On R3, include the serial link and all loopback interfaces.
R2(config)# router ospf 1
R2(config-router)# passive-interface default
*Jun 15 11:15:51.363: %OSPF-5-ADJCHG: Process 1, Nbr 192.168.40.1 on Serial0/1 from FULL to DOWN, Neighbor Down: Interface down or detached
R2(config-router)# no passive-interface s0/1
*Jun 15 11:15:56.130: %OSPF-5-ADJCHG: Process 1, Nbr 192.168.40.1 on Serial0/1 from LOADING to FULL, Loading Done
R2(config-router)# do sh run | s ospf 1
router ospf 1
passive-interface default
no passive-interface Serial0/1
network 172.16.23.0 0.0.0.255 area 0
network 172.16.100.0 0.0.0.255 area 10
R2(config-router)# no network 172.16.100.0 0.0.0.255 area 10
R2(config-router)# do sh run | s router
router ospf 1
passive-interface default
no passive-interface Serial0/1
network 172.16.23.0 0.0.0.255 area 0
R2(config-router)# end
R2# sh ip ospf neighbor
Neighbor ID Pri State Dead Time Address Interface
192.168.40.1 0 FULL/ - 00:00:30 172.16.23.3 Serial0/1
R2#
R3# conf t
Enter configuration commands, one per line. End with CNTL/Z.
R3(config)# router ospf 1
R3(config-router)# network 172.16.0.0 0.0.255.255 area 0
R3(config-router)# network 192.168.0.0 0.0.255.255 area 0
R3(config-router)# end
R3# sh ip ospf neighbor
Neighbor ID Pri State Dead Time Address Interface
172.16.100.1 0 FULL/ - 00:00:31 172.16.23.2 Serial0/1
R3#
Verification on router R2’s routing table.
R2# sh ip route ospf | b Gateway
Gateway of last resort is not set
172.16.0.0/16 is variably subnetted, 10 subnets, 2 masks
O 172.16.3.0/24 [110/1563] via 172.16.23.3, 00:25:17, Serial0/1
O 192.168.8.0/24 [110/1563] via 172.16.23.3, 00:25:00, Serial0/1
O 192.168.9.0/24 [110/1563] via 172.16.23.3, 00:25:00, Serial0/1
O 192.168.10.0/24 [110/1563] via 172.16.23.3, 00:25:00, Serial0/1
O 192.168.11.0/24 [110/1563] via 172.16.23.3, 00:25:00, Serial0/1
O 192.168.20.0/24 [110/1563] via 172.16.23.3, 00:25:00, Serial0/1
O 192.168.25.0/24 [110/1563] via 172.16.23.3, 00:25:00, Serial0/1
O 192.168.30.0/24 [110/1563] via 172.16.23.3, 00:25:00, Serial0/1
O 192.168.35.0/24 [110/1563] via 172.16.23.3, 00:25:00, Serial0/1
O 192.168.40.0/24 [110/1563] via 172.16.23.3, 00:25:00, Serial0/1
R2#
Allow One-Way Redistribution
On R2, let’s configure RIP to redistribute OSPF routes into RIP. Note that the metric is the default metric with which you want to originate the routes into RIP. If you do not specify a default metric in RIP, it gives routes an infinite metric and they are not advertised. Let’s give it a metric of 5.
R2# conf t
R2(config)# router rip
R2(config-router)# redistribute ospf 1 metric 5
R2(config-router)# end
*Jun 16 09:25:18.305: %SYS-5-CONFIG_I: Configured from console by console
R2# sh ip protocols | b rip
Routing Protocol is "rip"
Outgoing update filter list for all interfaces is not set
Serial0/0 filtered by (prefix-list) FILTER_172.23_->rip (per-user), default is not set
Incoming update filter list for all interfaces is not set
Sending updates every 30 seconds, next due in 24 seconds
Invalid after 180 seconds, hold down 180, flushed after 240
Redistributing: ospf 1 (internal, external 1 & 2, nssa-external 1 & 2)
Redistributing: rip
Default version control: send version 2, receive version 2
Interface Send Recv Triggered RIP Key-chain
Serial0/0 2 2
Automatic network summarization is not in effect
Maximum path: 4
Routing for Networks:
172.16.0.0
Passive Interface(s):
Serial0/1
Loopback0
Loopback100
Routing Information Sources:
Gateway Distance Last Update
Gateway Distance Last Update
172.16.12.1 120 00:00:09
Distance: (default is 120)
R2#
Let’s verify R1’s routing table to see if all OSPF routes are being propagated.
R1# sh ip route rip | b Gateway
Gateway of last resort is not set
172.16.0.0/16 is variably subnetted, 7 subnets, 2 masks
R 172.16.2.0/24 [120/1] via 172.16.12.2, 00:00:19, Serial0/0
R 172.16.3.0/24 [120/5] via 172.16.12.2, 00:00:19, Serial0/0
R 172.16.100.0/24 [120/1] via 172.16.12.2, 00:00:19, Serial0/0
R 192.168.8.0/24 [120/5] via 172.16.12.2, 00:00:19, Serial0/0
R 192.168.9.0/24 [120/5] via 172.16.12.2, 00:00:19, Serial0/0
R 192.168.10.0/24 [120/5] via 172.16.12.2, 00:00:19, Serial0/0
R 192.168.11.0/24 [120/5] via 172.16.12.2, 00:00:19, Serial0/0
R 192.168.20.0/24 [120/5] via 172.16.12.2, 00:00:19, Serial0/0
R 192.168.25.0/24 [120/5] via 172.16.12.2, 00:00:19, Serial0/0
R 192.168.30.0/24 [120/5] via 172.16.12.2, 00:00:19, Serial0/0
R 192.168.35.0/24 [120/5] via 172.16.12.2, 00:00:19, Serial0/0
R 192.168.40.0/24 [120/5] via 172.16.12.2, 00:00:19, Serial0/0
R1#
And sure enough, all routes are being propagated into RIP from OSPF, and the 172.16.23.0/24 segment is obviously being filter because that interface has an distribute list that will filter everything that is denied! Super!
Now, if we try to ping R3 Loopback from R1, it won’t work because R3 does not have information on how to get to R1 from Loopback 0. Let’s verify from both sides.
R1# ping 172.16.3.1
Type escape sequence to abort.
Sending 5, 100-byte ICMP Echos to 172.16.3.1, timeout is 2 seconds:
.....
Success rate is 0 percent (0/5)
R1#
R3# ping 172.16.1.1 source lo0
Type escape sequence to abort.
Sending 5, 100-byte ICMP Echos to 172.16.1.1, timeout is 2 seconds:
Packet sent with a source address of 172.16.3.1
.....
Success rate is 0 percent (0/5)
R3#
There are several ways we can solve this problem. We can originate a default route into OSPF that points toward R2 so that the pings are routed back toward R2. R2 uses its information from RIPv2 to send pings back to R1.
Let’s force R2 to advertise a default route in OSPF.
R2(config)# router ospf 1
R2(config-router)# default-information originate always
Note: By configuring the default-information originate command, OSPF injects a default route into OSPF if it exists on the routing table. If you add the always syntax OSPF will inject a default route into OSPF even if there is none configured. Let’s try pinging R3’s loopback again from R1.
R1> ping 172.16.3.1
Type escape sequence to abort.
Sending 5, 100-byte ICMP Echos to 172.16.3.1, timeout is 2 seconds:
!!!!!
Success rate is 100 percent (5/5), round-trip min/avg/max = 58/62/68 ms
R1>
Successful as expected. We should now have full reachability within the lab. Test it out! If you don’t, just remove the distribute list under rip process on R2 ;)
Mutual Redistribution Between RIP and OSPF
Now, I’m going to redistribute RIP into OSPF and remove that default route from OSPF issued with the default-information originate always command. We will have redistribution on both protocols. Keep in mind that you should only redistribute between protocols if you really have no other choice. After configuration on R2, verify R3’s routing table.
R2# conf t
Enter configuration commands, one per line. End with CNTL/Z.
R2(config)# router ospf 1
R2(config-router)# no default-information originate always
R2(config-router)# redistribute rip
R2(config-router)# do sh run | s ospf 1
router ospf 1
redistribute rip subnets
passive-interface default
no passive-interface Serial0/1
network 172.16.23.0 0.0.0.255 area 0
R2(config-router)#
R3> sh ip route ospf | b Gateway
Gateway of last resort is not set
172.16.0.0/16 is variably subnetted, 8 subnets, 2 masks
O E2 172.16.1.0/24 [110/20] via 172.16.23.2, 00:01:54, Serial0/1
O E2 172.16.2.0/24 [110/20] via 172.16.23.2, 00:01:54, Serial0/1
O E2 172.16.12.0/24 [110/20] via 172.16.23.2, 00:01:54, Serial0/1
O E2 172.16.100.0/24 [110/20] via 172.16.23.2, 00:01:54, Serial0/1
O E2 192.168.48.0/22 [110/20] via 172.16.23.2, 00:01:54, Serial0/1
O E2 192.168.70.0/24 [110/20] via 172.16.23.2, 00:01:54, Serial0/1
R3>
Note: The redistribute rip command automatically puts the subnets syntax by default on IOS Version 15.4(2)T4, which is what I am running on IOU. I purposely showed the running configuration to observe this behaviour.
If you have an older version, and If you display the routing table on R3, the external OSPF routes that were added are should be 192.168.70.0/24 and 192.168.48.0/22 networks.
This is because, by default, OSPF only accepts classful networks and supernets when redistributing into it.
The only classful network coming into R2 from RIP is the class C network 192.168.70.0, and the only supernet is the 192.168.48.0/22. You can modify this behavior by adding the subnets keyword to the redistribute command. You should again have full connectivity between all networks in the diagram, use the Tcl script on each router to verify full connectivity.
Set a Default Seed Metric
Under any routing protocol, you can specify a default seed metric to be used for redistribution instead of setting metrics on a per-protocol basis. A seed metric is a protocol-independent feature of the Cisco IOS that is usually configured when redistributing into distance-vector protocols.
Notice that the metric listed on R3’s routing table is 20.
R3> sh ip route ospf | b Gateway
Gateway of last resort is not set
172.16.0.0/16 is variably subnetted, 8 subnets, 2 masks
O E2 172.16.1.0/24 [110/20] via 172.16.23.2, 00:27:13, Serial0/1
O E2 172.16.2.0/24 [110/20] via 172.16.23.2, 00:27:13, Serial0/1
O E2 172.16.12.0/24 [110/20] via 172.16.23.2, 00:27:13, Serial0/1
O E2 172.16.100.0/24 [110/20] via 172.16.23.2, 00:27:13, Serial0/1
O E2 192.168.48.0/22 [110/20] via 172.16.23.2, 00:27:13, Serial0/1
O E2 192.168.70.0/24 [110/20] via 172.16.23.2, 00:27:13, Serial0/1
R3>
You can override the global creation of a default seed metric on a per-protocol basis by using the metric argument in a redistribution command or you can use the metric command under other routing protocols.
On R2, in OSPF configuration mode, configure the default metric for redistributed routes. The default metric for all OSPF redistributed routes is 20, except for BGP, which is 1. Setting the metric for RIP to a higher number makes it less preferable to routes redistributed from other routing protocols.
R2# conf t
R2(config)# router ospf 1
R2(config-router)# default-metric 555
R2(config-router)#
Verify the new metric on R3’s routing table. It might take some time for the new metric to propagate so, let’s clear the OSPF process to accelerate the update.
R3# clear ip ospf process
Reset ALL OSPF processes? [no]: yes
R3#
*Jun 16 14:57:30.789: %OSPF-5-ADJCHG: Process 1, Nbr 172.16.100.1 on Serial0/1 from FULL to DOWN, Neighbor Down: Interface down or detached
*Jun 16 14:57:30.949: %OSPF-5-ADJCHG: Process 1, Nbr 172.16.100.1 on Serial0/1 from LOADING to FULL, Loading Done
R3# sh ip route ospf | b Gateway
Gateway of last resort is not set
172.16.0.0/16 is variably subnetted, 8 subnets, 2 masks
O E2 172.16.1.0/24 [110/555] via 172.16.23.2, 00:00:05, Serial0/1
O E2 172.16.2.0/24 [110/555] via 172.16.23.2, 00:00:05, Serial0/1
O E2 172.16.12.0/24 [110/555] via 172.16.23.2, 00:00:05, Serial0/1
O E2 172.16.100.0/24 [110/555] via 172.16.23.2, 00:00:05, Serial0/1
O E2 192.168.48.0/22 [110/555] via 172.16.23.2, 00:00:05, Serial0/1
O E2 192.168.70.0/24 [110/555] via 172.16.23.2, 00:00:05, Serial0/1
R3#
Change the OSPF External Network Type
Look at R3’s routing table. Notice that the External (redistributed) routes have O E2 as their type. In the output, E2 means External, Type 2. OSPF has two external metric types, and E2 is the default. OE1 metrics increase the metric as they traverse the path, whereas OE2 metrics do not increase as they get advertised through the OSPF domain, according to RFC 2328 Section 16.4.1 .
Let’s now change the External Type routes, change the type to E1 for RIP redistributed routes.
R1# conf t
R1(config)# router ospf 1
R1(config-router)# redistribute rip metric-type 1
R1(config-router)#
Let’s verify R3’s routing table for those external type 1 routes.
R3# sh ip route ospf | b Gateway
Gateway of last resort is not set
172.16.0.0/16 is variably subnetted, 8 subnets, 2 masks
O E1 172.16.1.0/24 [110/2117] via 172.16.23.2, 00:00:39, Serial0/1
O E1 172.16.2.0/24 [110/2117] via 172.16.23.2, 00:00:39, Serial0/1
O E1 172.16.12.0/24 [110/2117] via 172.16.23.2, 00:00:39, Serial0/1
O E1 172.16.100.0/24 [110/2117] via 172.16.23.2, 00:00:39, Serial0/1
O E1 192.168.48.0/22 [110/2117] via 172.16.23.2, 00:00:39, Serial0/1
O E1 192.168.70.0/24 [110/2117] via 172.16.23.2, 00:00:39, Serial0/1
R3#
Notice that the external type 1 routes are now displaying a more accurate metric of 2117.
Hope this helps someone else!